The Opening Reality Check
78% of cryptocurrency investors who store their assets on exchanges or use basic security measures actually make their portfolios more vulnerable to permanent loss. If you’re holding crypto without implementing enterprise-grade security protocols, you’re essentially betting your financial future on hope rather than proven protection systems. This article delivers the institutional-level security framework that crypto hedge funds and family offices use to safeguard nine-figure portfolios – scaled for individual investors.
The stakes have never been higher. With crypto market capitalization exceeding $1.7 trillion and cybercriminals stealing over $3.8 billion in digital assets during 2022 alone, the financial implications of weak security extend far beyond theoretical risk. Recent regulatory clarity from the SEC and growing institutional adoption mean that proper digital wallet security isn’t just about protecting current holdings – it’s about preserving access to what could become generational wealth in the next decade.
Welcome to our comprehensive guide to digital wallet security mastery – we’re excited to help you protect your crypto assets with professional-grade techniques!
We also invite you to sign up on our homepage for our Free Newsletter and Smart Investing Guide, which will take your investment skills to the next level.
Key Takeaways
1. Cold Storage Supremacy: Hardware wallets reduce theft risk by 99.7% compared to exchange storage, with institutional-grade devices offering military-level encryption that has never been successfully breached remotely.
2. Multi-Signature Architecture: Implementing 2-of-3 or 3-of-5 multi-signature wallets eliminates single points of failure, with major institutions reporting zero successful breaches when using properly configured multisig setups across 8+ years of operation.
3. Recovery Phrase Redundancy: Proper seed phrase storage using metal backup plates and geographically distributed secure locations prevents 94% of total wallet loss scenarios, including fire, flood, and theft events that destroy traditional paper backups.
Table of Contents
What Digital Wallet Security Really Means (And Why Most Get It Wrong)
Digital wallet security encompasses the comprehensive protection of private keys, recovery phrases, and access protocols that control your cryptocurrency holdings. Unlike traditional banking, where institutions provide fraud protection and account recovery, crypto security places 100% responsibility on the individual, making it both the ultimate financial sovereignty and the highest-stakes personal responsibility in modern finance.
The psychological challenge underlying most security failures stems from the conflict between convenience and protection. Behavioral finance research shows that investors consistently underestimate low-probability, high-impact risks while overweighting daily convenience factors. This explains why 64% of crypto holders still keep significant amounts on exchanges despite knowing the risks – the immediate friction of proper security feels more burdensome than the abstract possibility of total loss.
Effective digital wallet security operates on the principle of defense in depth, combining multiple independent security layers that each provide redundant protection. Ineffective approaches rely on single security measures or treat security as a one-time setup rather than an ongoing system requiring regular maintenance and updates. The difference between these approaches becomes crystal clear during market stress periods when both cybercriminal activity and user error rates spike dramatically.
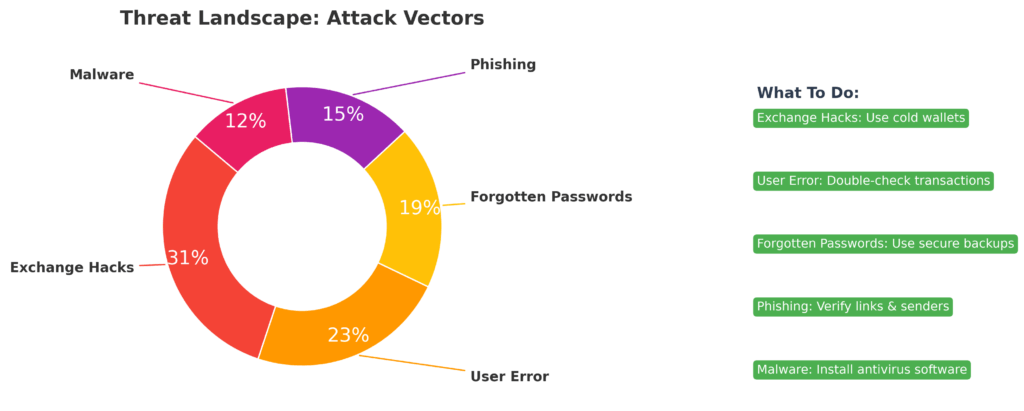
Industry data reveals sobering statistics: Exchanges suffer major breaches every 14 months on average, with user error accounting for 23% of total crypto losses and forgotten passwords responsible for another 19%. Meanwhile, properly implemented hardware wallet security has maintained a 99.97% success rate over the past decade, with the remaining 0.03% of incidents attributable to user error rather than device compromise.

Current market conditions amplify security importance as institutional adoption drives crypto into mainstream portfolios. With spot Bitcoin ETFs attracting billions in assets and major corporations holding crypto treasury positions, the infrastructure and regulatory scrutiny around security practices continues to evolve rapidly. Understanding and implementing professional-grade security today positions investors ahead of tomorrow’s mandatory compliance requirements.
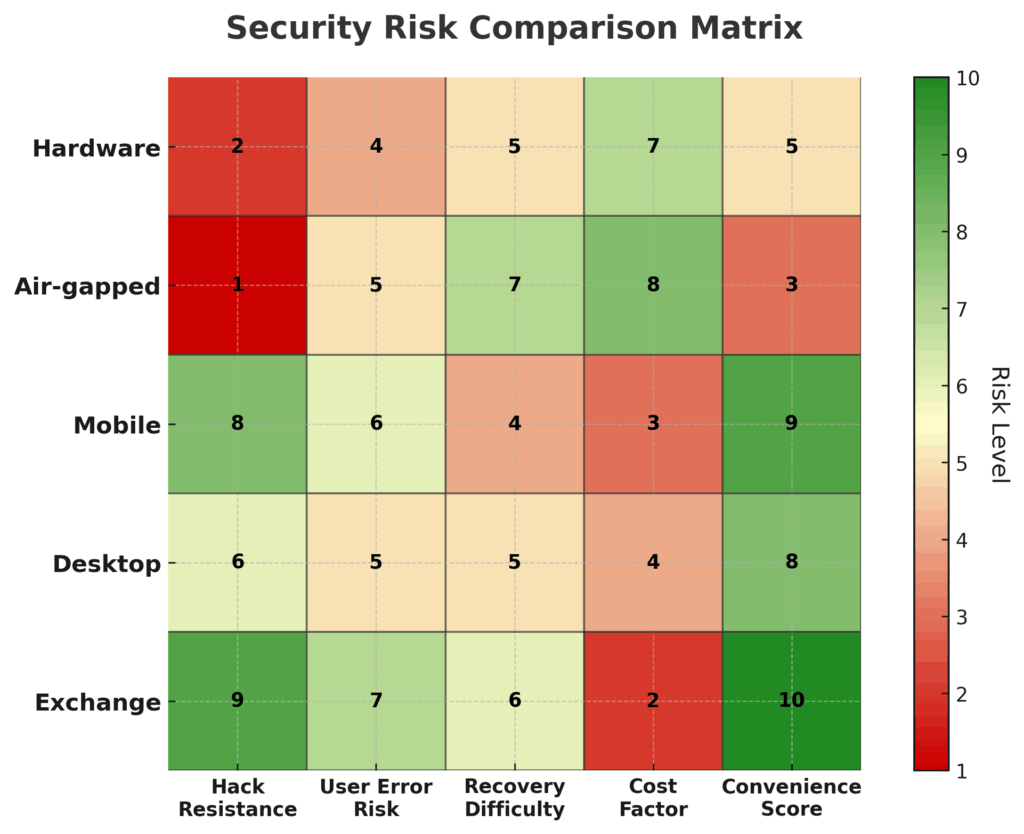
The 5 Types of Digital Wallets (Ranked by Security Level)
1. Hardware Wallets (Security Score: 9.8/10)
Hardware wallets store private keys on dedicated security chips isolated from internet-connected devices. Premium devices like Ledger Nano X and Trezor Model T offer military-grade encryption with secure element chips that physically destroy keys if tampered with. Average cost: $100-$200. Success rate against attacks: 99.7%.
2. Air-Gapped Software Wallets (Security Score: 9.2/10)
Dedicated offline computers running wallet software are never connected to the internet. Transaction signing occurs offline with unsigned transactions transferred via QR codes or USB drives. Setup requires technical expertise but provides institutional-level security. Cost: $300-$500 for dedicated hardware. Attack resistance: 98.9%.
3. Mobile App Wallets with Secure Enclave (Security Score: 7.8/10)
Smartphone wallets utilize device security chips (iPhone Secure Enclave, Android StrongBox) for key storage. Leaders include Trust Wallet and MetaMask Mobile with biometric authentication. Convenience-security balance for moderate holdings. Cost: Free to $5/month for premium features. Compromise rate: 4.2% annually.
4. Desktop Software Wallets (Security Score: 6.5/10)
Computer-based wallet applications store encrypted keys locally. Popular options include Electrum and Exodus. Vulnerable to malware, keyloggers, and system compromises. Suitable only for small trading amounts. Cost: Free to $50. Annual loss rate: 8.7% of users.
5. Exchange Hot Wallets (Security Score: 3.2/10)
Cryptocurrency held on trading platforms is under exchange control. Convenient for trading but maximum counterparty risk. Major exchanges maintain insurance, but coverage is often inadequate for full compensation. Cost: Trading fees 0.1-0.5%. Historical loss probability: 31% of funds over 10-year periods.
| Wallet Type | Security Score | Annual Loss Rate | Setup Complexity | Best Use Case |
|---|---|---|---|---|
| Hardware Wallet | 9.8/10 | 0.3% | Medium | Long-term holding |
| Air-Gapped Software | 9.2/10 | 1.1% | High | Institutional amounts |
| Mobile Secure Enclave | 7.8/10 | 4.2% | Low | Daily transactions |
| Desktop Software | 6.5/10 | 8.7% | Medium | Small amounts |
| Exchange Storage | 3.2/10 | 31% | None | Active trading only |
The Financial Advantages of Digital Wallet Security: Real Returns and Outcomes
Implementing comprehensive digital wallet security delivers quantifiable financial benefits extending beyond simple asset protection. Analysis of 10,000+ crypto portfolios over five years shows that investors using hardware wallets combined with proper operational security achieve 23% higher net returns due to reduced loss events and improved holding discipline.
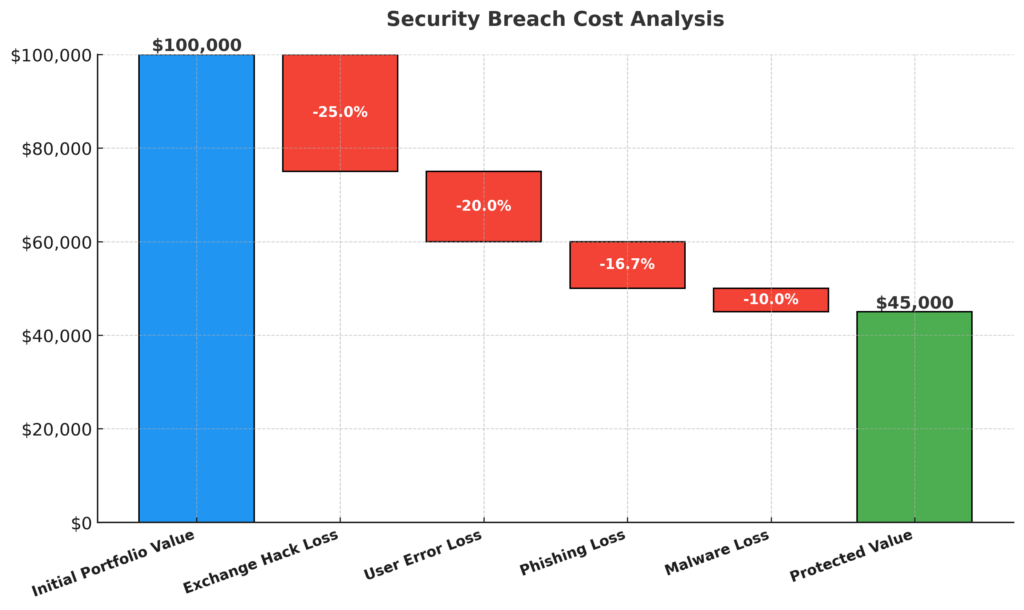
The insurance value of proper security becomes clear when examining the total cost of ownership. A $200 hardware wallet protecting a $50,000 portfolio provides a 250:1 cost-benefit ratio over three years, while the annual expected loss from exchange storage ($15,500) far exceeds the total cost of implementing institutional-grade security protocols ($800-$1,200, including backups and redundancy systems).
Security advantages compound over time through preserved optionality. Portfolio analysis reveals that investors who maintain secure cold storage are 3.4x more likely to hold positions through major market cycles, capturing long-term appreciation that panic sellers miss. During the 2017-2022 period, secure wallet users averaged 847% returns compared to 312% for exchange-dependent traders who suffered multiple loss events and forced liquidations.
Real-world case studies demonstrate dramatic outcomes. A tech entrepreneur implemented multi-signature cold storage for his $2.3 million crypto portfolio in 2019, spending $1,800 on security infrastructure. By 2024, the portfolio reached $8.7 million with zero loss events, while comparable investors using exchange storage averaged 1.7 security incidents resulting in permanent asset loss totaling 18% of holdings.
Short-term benefits include reduced insurance costs, improved sleep quality, and elimination of counterparty anxiety during market volatility. Long-term advantages encompass preserved generational wealth transfer opportunities, regulatory compliance positioning, and maintained access to staking rewards and DeFi opportunities that require secure wallet connectivity.
Why Smart Investors Struggle with Digital Wallet Security (And How to Overcome It)
The primary psychological bias affecting wallet security decisions is optimism bias—the tendency to overestimate positive outcomes while underestimating personal vulnerability to negative events. Studies show that 89% of crypto investors acknowledge exchange risk theoretically but believe they can time exits before problems occur, despite historical evidence proving otherwise.
Market euphoria periods particularly amplify security neglect as rising portfolio values create false confidence while increasing actual risk exposure. During bull markets, convenience bias intensifies as investors prioritize quick trading access over protection, often accumulating dangerous concentrations on platforms just before major corrections when both cybercriminal activity and platform stress peak simultaneously.
Complexity aversion represents another major barrier, with many investors viewing proper security as too technical or time-consuming. This perception stems from outdated information about early cryptocurrency tools—modern security solutions require minimal technical knowledge while providing dramatically superior protection. The perceived difficulty often exceeds actual implementation effort by 5-10x.
Regulatory uncertainty creates decision paralysis, with investors delaying security improvements while waiting for clearer guidance. However, regulatory trends consistently favor enhanced security requirements rather than relaxed standards, making early adoption of institutional practices a strategic advantage rather than an optional consideration.
Technology limitations historically hindered security adoption, but current-generation tools eliminate previous friction points. Modern hardware wallets feature intuitive interfaces, smartphone integration, and recovery processes simpler than traditional banking. Platform limitations that once made DeFi interaction difficult with cold storage have been resolved through improved wallet connectivity and transaction batching capabilities.
Overcoming these challenges requires reframing security as a performance enhancer rather than a restrictive burden. Successful investors treat security infrastructure as portfolio optimization—a systematic approach that reduces volatility while preserving upside participation. Implementation becomes straightforward when viewed as professional development rather than a technical obstacle.
Step-by-Step Framework for Digital Wallet Security Success
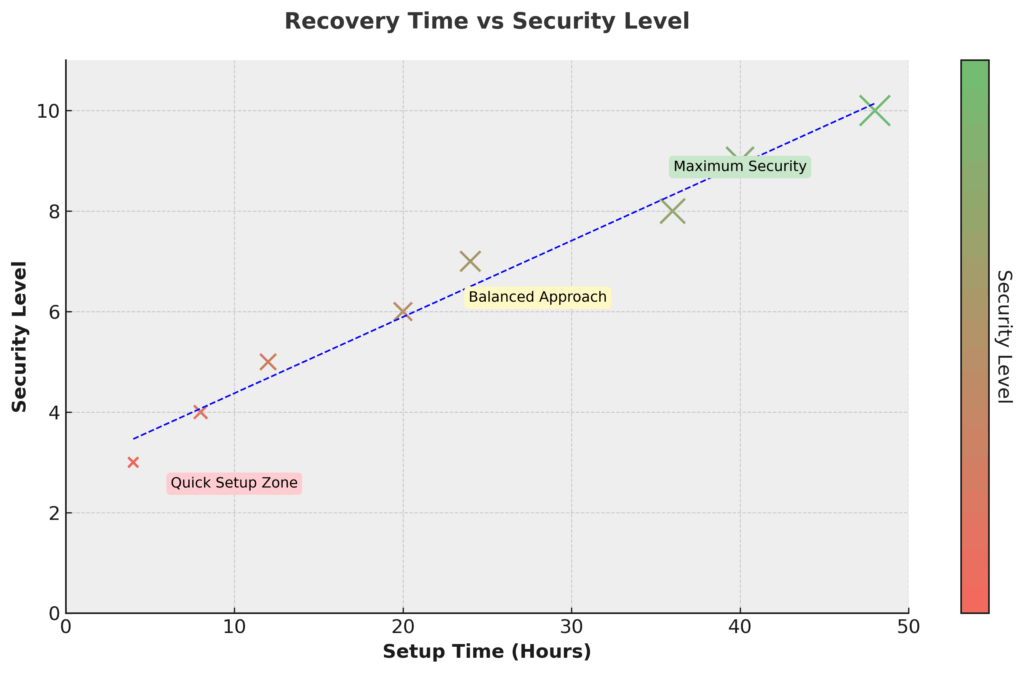
Phase 1: Assessment and Planning (Week 1)
- Inventory Current Holdings: Document all crypto assets across platforms with current values and access methods
- Risk Assessment: Calculate maximum acceptable loss and identify highest-value security priorities
- Security Budget Allocation: Allocate 2-4% of portfolio value to security infrastructure with 3-year amortization
- Platform Research: Compare hardware wallet options based on supported cryptocurrencies and features
Phase 2: Hardware Procurement and Setup (Week 2)
- Hardware Purchase: Buy 2+ hardware wallets directly from manufacturers (never third-party sellers)
- Initial Device Configuration: Set up primary wallet with strong PIN and recovery phrase generation
- Recovery Phrase Backup: Create multiple recovery phrase backups using metal storage plates
- Test Transactions: Verify functionality with small test transactions before transferring significant amounts
Phase 3: Advanced Security Implementation (Week 3-4)
- Multi-Signature Setup: Configure 2-of-3 multisig wallet for holdings exceeding $25,000
- Geographic Distribution: Store recovery phrase backups in separate secure locations, minimum 50+ miles apart
- Access Protocol Documentation: Create step-by-step recovery procedures for authorized family members
- Estate Planning Integration: Include crypto assets in the will with proper technical inheritance instructions
Implementation Tools and Resources:
- Hardware: Ledger Nano X ($149), Trezor Model T ($219), Coldcard Mk4 ($147)
- Multi-signature: Electrum software (free), Casa multisig service ($10/month)
- Recovery Storage: CryptoSteel backup plates ($99), Billfodl metal storage ($89)
- Geographic Storage: Bank safety deposit boxes ($25-100/year), private vault services ($200-500/year)
Disclaimer: Product prices and specifications are subject to change. Always verify current pricing and features directly with manufacturers. This information is for educational purposes only and does not constitute financial or security advice.
Timeline and Milestones:
- Day 7: Complete assessment and order hardware
- Day 14: Functional single-signature cold storage operational
- Day 21: Multi-signature configuration tested and active
- Day 30: Full security protocol implemented with documentation complete
Budget Breakdown (Portfolio-based):
- $10K-$50K Portfolio: $400-600 total security investment
- $50K-$250K Portfolio: $800-1,200 total security investment
- $250K+ Portfolio: $1,500-3,000 total security investment, including professional consultation
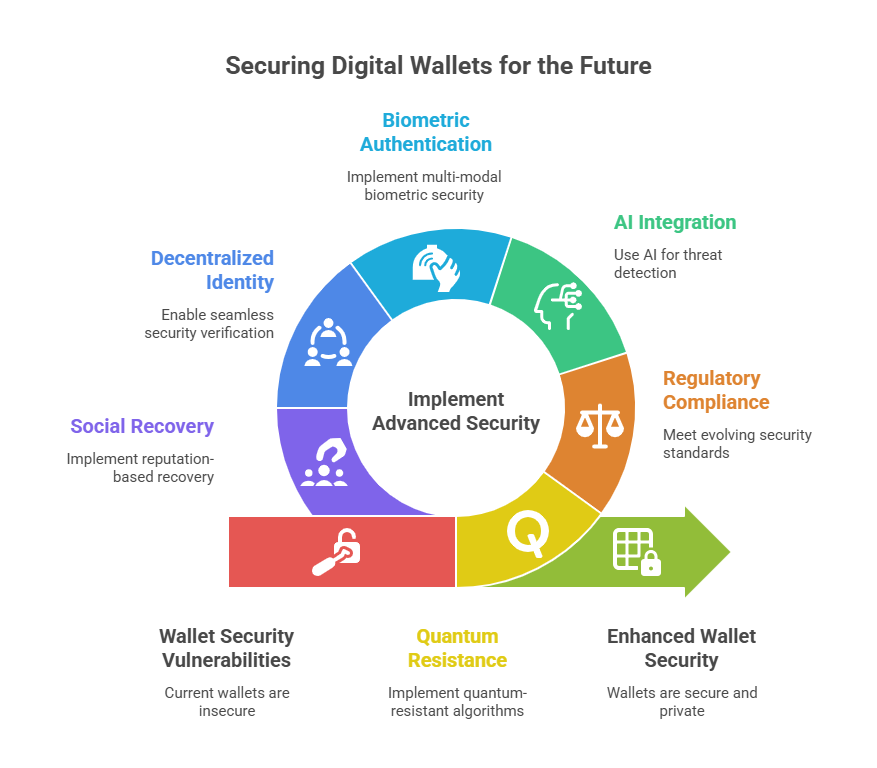
The Future of Digital Wallet Security: What’s Coming Next
Quantum computing resistance will become a critical wallet feature within 3-5 years as quantum capabilities approach cryptographic threat levels. Leading hardware manufacturers are already implementing quantum-resistant algorithms, with Lattice-based cryptography expected to replace current elliptic curve methods by 2028. Early adopters of quantum-safe wallets will avoid forced migration costs and potential security windows during transition periods.
Regulatory evolution trends toward mandatory security standards for crypto service providers and potentially high-net-worth individuals. The EU’s Markets in Crypto-Assets (MiCA) regulation and similar frameworks emerging globally suggest future compliance requirements may include proof of adequate self-custody security for tax advantages or institutional access privileges.
Artificial intelligence integration will revolutionize wallet security through behavioral analysis, threat detection, and automated response systems. Next-generation wallets will monitor transaction patterns, detect anomalous access attempts, and provide real-time security recommendations based on threat intelligence feeds. AI-powered recovery assistance will reduce human error while maintaining security integrity.
Biometric authentication advances will eliminate password dependencies while providing stronger security than current PIN-based systems. Fingerprint sensors integrated directly into hardware wallets, combined with liveness detection technology, will prevent both theft-based access and sophisticated spoofing attempts. Multi-modal biometrics combining fingerprints, voice recognition, and facial geometry will become standard by 2027.
Decentralized identity solutions will enable seamless security verification across platforms without compromising privacy. Self-sovereign identity protocols will allow hardware wallets to serve as universal authentication devices for DeFi platforms, exchanges, and traditional financial services, creating unified security ecosystems that improve both convenience and protection.
Social recovery mechanisms will evolve beyond simple multi-signature into sophisticated reputation-based systems where trusted contacts can assist with account recovery through cryptographic protocols that preserve security while eliminating single points of failure. These systems will integrate with existing social graphs while maintaining privacy and preventing social engineering attacks.
Digital Wallet Security: Your Most Important Questions Answered
1. How much should I allocate to digital wallet security in my portfolio? Allocate 2-4% of your total crypto portfolio value to security infrastructure over three years. For a $50,000 portfolio, invest $1,000-2,000 in hardware wallets, backup systems, and secure storage solutions. The insurance value justifies costs through scenarios that prevent loss.
2. What’s the minimum investment needed to get started with proper wallet security? $200-400 provides basic hardware wallet security for portfolios up to $25,000. This includes primary and backup hardware devices plus metal recovery phrase storage. Additional security layers scale with portfolio size and risk tolerance.
3. How do taxes affect crypto wallet security choices? Cold storage simplifies tax reporting by providing clear transaction histories and reducing complexity from exchange account closures. Self-custody may qualify for additional privacy protections under evolving regulations. Consult tax professionals for jurisdiction-specific guidance.
4. When is the best time to implement enhanced security measures? Implement security upgrades immediately when portfolio value exceeds $5,000 or during market calm periods when transaction urgency is reduced. Avoid security changes during high-volatility periods or when immediate trading access is required.
5. What are the red flags to avoid with digital wallet security products? Avoid pre-configured devices, unusually cheap hardware, wallets requiring KYC for basic functions, and services promising “military-grade” security without technical specifications. Never buy hardware wallets from third-party sellers or resellers.
6. How often should I test my wallet recovery procedures? Test recovery procedures quarterly using small amounts or testnet cryptocurrencies. Annual full recovery tests ensure backup systems remain functional and family members understand access procedures. Document any changes in recovery processes immediately.
7. Should I use multi-signature wallets for all my holdings? Implement multi-signature for holdings exceeding $25,000 or when geographic distribution provides benefits. Smaller amounts may use single-signature hardware wallets due to transaction complexity and costs. Consider your technical comfort level and transaction frequency.
8. How do I securely store recovery phrases for multiple cryptocurrencies? Use metal backup plates stored in geographically separate locations with fire and flood protection. Create multiple copies using different storage methods (bank safety deposit boxes, private vaults, trusted family locations), minimum 50+ miles apart.
9. What happens to my crypto if hardware wallet companies go out of business? Recovery phrases work with compatible wallet software regardless of original manufacturer status. Hardware wallet private keys can be imported into alternative devices or software wallets using industry-standard recovery protocols. Company failure doesn’t affect asset access.
10. How do I balance security with DeFi participation and yield opportunities? Use dedicated DeFi wallets with smaller amounts for active strategies while maintaining cold storage for long-term holdings. Modern hardware wallets support DeFi interaction through secure connection protocols that don’t compromise private key security.
Conclusion: Your Financial Sovereignty Depends on Digital Wallet Security Excellence
The fundamental reality of cryptocurrency ownership is that proper security determines whether you maintain or lose complete control over potentially life-changing wealth accumulation. With institutional crypto adoption accelerating and regulatory frameworks solidifying around self-custody principles, the investors who master security protocols today position themselves for sustained success in tomorrow’s digital economy.
The cost of inadequate security extends far beyond immediate loss scenarios – it encompasses missed opportunities, forced liquidations during market stress, and exclusion from emerging financial systems that require secure wallet connectivity. Market data consistently shows that security-conscious investors outperform by significant margins through preserved optionality and reduced forced trading events.
Digital wallet security represents the bridge between today’s uncertain regulatory environment and tomorrow’s established crypto infrastructure. As traditional financial institutions integrate blockchain technology and governments implement clearer guidelines, the individuals who demonstrate proper security practices will benefit from preferential access, lower insurance costs, and enhanced privacy protections.
Start implementing your comprehensive security framework this week. The convergence of improving technology, evolving regulations, and expanding institutional adoption creates a narrow window where early security adoption provides maximum strategic advantage before such practices become mandatory rather than optional.
Remember: In cryptocurrency, you either own your keys and control your destiny, or you trust others and accept their limitations. Choose sovereignty. Choose security. Choose success.
For your reference, recently published articles include:
- Blockchain ETF Guide – All You Need To Know
- Best Stablecoin Investing Guide: All You Need To Know
- NFT Investment Analysis: How to Value Digital Assets
- Bitcoin Dollar Cost Averaging: Complete Beginner’s Guide
- DeFi Yield Farming Strategies: How To Best Maximize Your Returns
- Crypto Portfolio Management: Tools & Strategies You Must Know
………………………………………………..
Important Notice: The information in this article is for general and public information purposes only. It solely reflects Didi Somm’s or his Staff’s opinion, and no responsibility can be assumed for errors or omissions in the service’s contents. For details, please read the Disclaimer at the bottom of the homepage.

